proxy hacking
What is proxy hacking?
Proxy hacking is a cyber attack technique designed to supplant an authentic webpage in a search engine's index and search results pages to drive traffic to an imitation site.
In the worst case, an attacker may use proxy hacking to introduce malware or other viruses to the victim's computer. In a less malicious but still devious example, the attacker may try to gain an advantage over a competitor or get advertising revenue by redirecting traffic to their fraudulent website. The latter is also known as SEO hijacking, Content scraping, page hijacking or pagejacking, and is distinct from watering hole attacks, attack proxies, web proxies or attacks via proxy.
The term proxy hacking was first popularized by SEO expert Dan Thies. He identified this type of black hat SEO attack in 2006 and publicly exposed it in 2007.

How does proxy hacking work?
In a proxy hack, the attacker duplicates a highly ranked search result webpage, and tries to get their copy to rank higher in a search than the original. The goal of the attacker is to get victims to go to the imitation website instead of the original. This may be with the simple goal of getting advertisement revenue or paid referral links from stolen content. Alternatively, the attacker may try to use the page to introduce malware or other viruses to the victim's computer. There are two main ways that the attacker duplicates the content -- by using a malicious web proxy or by outright duplicating the target content.
In the original form of a proxy hack, the attacker creates a malicious web proxy that points to the target victim page. The attacker then creates links to their proxied URL that claims to be the original content. When the search engine indexer checks the links to the proxy, it is seen as having the same content as the victim page. This method of proxy hacking has been mostly mitigated by changes to Google's ranking algorithm.
In another form of proxy attack, the attacker creates a duplicate of the targeted webpage on another web server. The entire content of the site is copied instead of just linked or proxied. Large proxy hacking operations may use content scraping to automatically steal and reproduce webpages.
Regardless of the method of duplicating the content, the attacker then attempts to make their copy rank higher in Google search or other search engines than the original website. Proxy hacking pages use a variety of methods to rank higher than the original webpage.
The domain may be more authoritative due to age or backlinks. They may use black hat SEO techniques, such as keyword stuffing or link farming. URL hijacking may be used to take advantage of 302 redirect links to make the search engine think that the copy site is the original content. Eventually the authentic page will rank lower and may be seen as duplicated content, in which case a search engine may remove it from its index completely.
How to defend against proxy hacking
There is no way to fully protect a site against proxy hacking and duplicated content, as it is done on sites the original site owners do not control and third-party search engines. But, by following SEO best practices, a company can defend against and reduce the efficacy of proxy hacking.
Site owners can raise their domain's authoritativeness to make it more difficult for hijackers to rank higher. This means using white hat SEO optimization. They can use high quality keywords and links and a sitemap to make canonical links clear and reduce the effect of 302 URL hijacking attempts.
Organizations should protect their domain against automated content scraping. This can mean blocking malicious bots and spiders from accessing their site. They need to block malicious web proxies and use scrape shields to obfuscate content. Many web servers and content delivery networks (CDNs) now offer malicious bot fighting and filtering tools that can help to stop proxy hacking.
Site owners also should perform regular SEO audits. These can reveal potential proxy hacking attempts.
When a site owner suspects that their website is the victim of a proxy hack, they should search for a phrase that should be unique, or almost unique, to their own content. Their page should be prominent in search results. If, however, a duplicate of that content shows up, it may be a proxy page.
Proxy page URLs typically look different from genuine pages. They often contain the full link to another domain. For example, a malicious link may appear similar to www.examplebadsite.com/nph-proxy/http/www.techtarget.com/definition. Notice how the middle of the link contains http and www which normally only appear at the start of the link and .com which should be at the end of the domain name.
Other attacks similar to proxy hacking
There are several concepts that sound similar to proxy hacking or work in a similar manner.
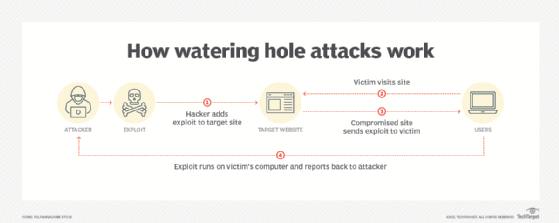
Watering hole attacks are similar because they also seek to take advantage of sites that the victim user is trying to go to. In watering hole attacks, the attacker hacks the original website server and changes it to serve malicious content instead of copying the content.
Typosquatting uses a similar looking or easy-to-mistype URL of a popular website to serve fraudulent websites. Targeted proxy hacking may also employ typosquatting in addition to duplicating content.
Malicious proxies, or man-in-the-middle attacks, do not copy the content to another website. Instead, they sit between the victim site and the user and intercept and modify the content before the user sees it. Their goal is to be invisible to the user of the site, not to change search engine ranking.
Attack proxy is a tool used by hackers to automatically scan and attack a website. They can apply common attacks and check for vulnerabilities of a site or server. Popular attack proxies are OWASP Zed Attack Proxy and Burp Suite by PortSwigger.
Hacking via proxy, or using a proxy, is when an attacker uses another computer rather than their own to perform the attack. This may be a dedicated attack computer or another victim's computer that the attacker uses as a jumping-off point to perform another attack.
See also: scraper site, site scraper, session hijacking, cache poisoning, IP spoofing, content spoofing, ingress filtering, cyber hijacking and browser hijacking.








